Virtualization, Cloud, Infrastructure and all that stuff in-between
My ramblings on the stuff that holds it all together
POSH1Liner – Count the number of resource groups in a subscription
If you ever need a quick count of the number of resource groups in your current subscription (get-azContext) to check you can use the following command to get a quick check.
(get-AzResourceGroup).count
This is especially useful if you’re using a shared subscription that may be pushing the 980 resource group limit and you want to check before a script runs.
One Button Access to Copilot on iPhone
So far I’ve found Apple Intelligence a bit underwhelming. Copilot however, has access to all my work context, emails, Teams messages, my calendar etc. so I’d like quick access to use it – there is no way to replace Apple Intelligence wholesale yet
Disclaimer: Yes, I am a Microsoft employee, but this is just something I find useful, other AI’s are available.
You can get quick access to Copilot by configuring the Action Button on recent iPhones to launch the M365 Copilot app. (note there is a difference between the two Copilot apps available on the iPhone.

‘Consumer’ Copilot is free other than needing a Microsoft personal account and only has access to data from the Internet (‘consumer’ may not be the correct marketing name)

M365 Copilot app requires a paid-for license but can search work content (only the content you have access to)
On the iPhone you can go to settings, type ‘Action Button’ and select it
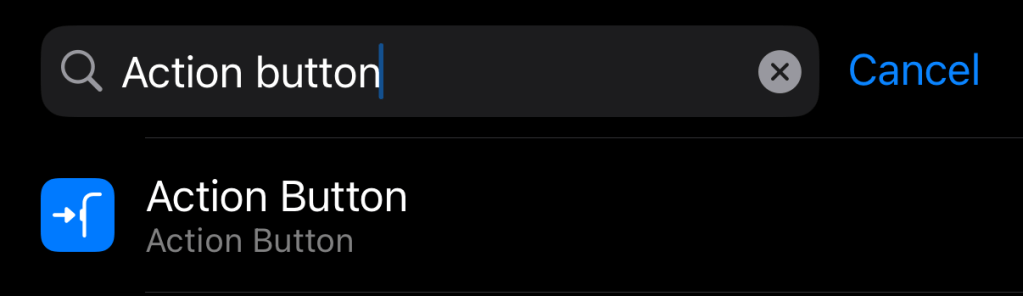
Then swipe left/right to find the ‘Shortcut’ option and tap

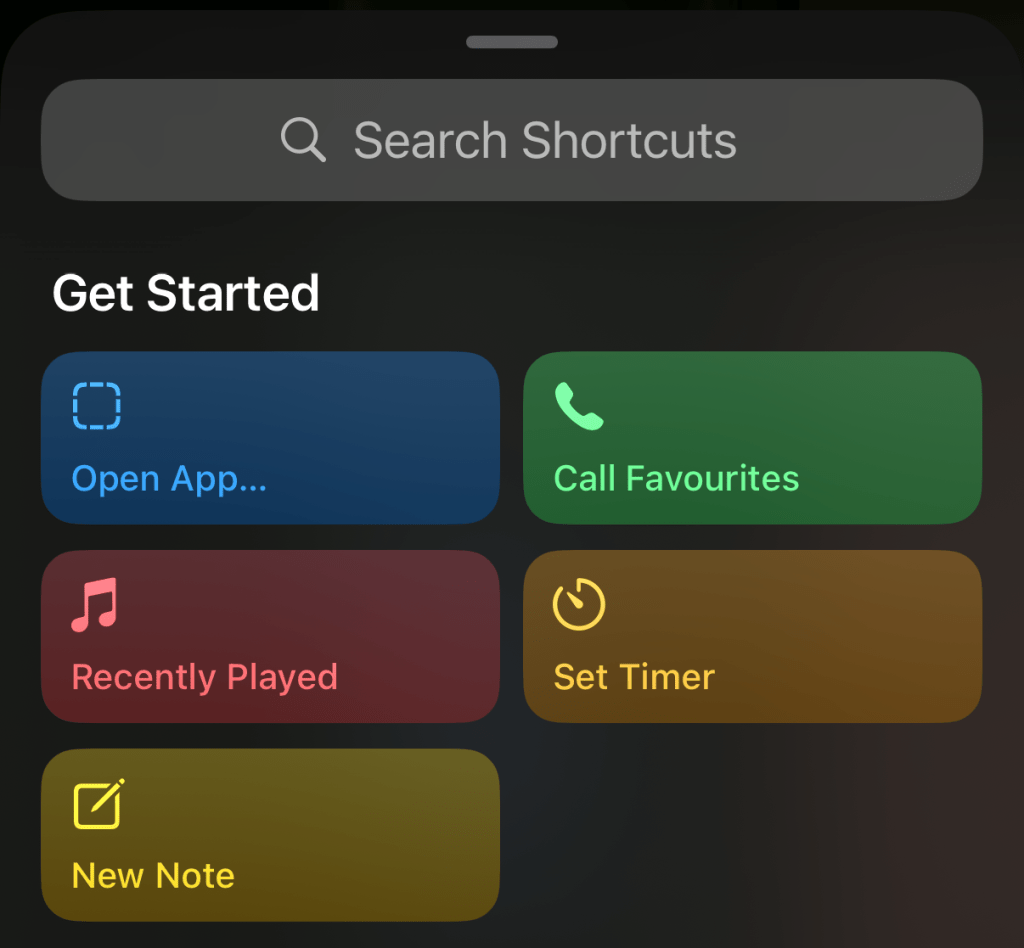
‘Open App’ from the shortcuts screen and choose the M365 Copilot app from the list (search if you have a lot of apps)
Now, when you press the Action Button you’re put directly into the M365 Copilot app, it doesn’t default to voice search so you have to type your prompt, or press the microphone button to use your voice.
Set Windows keyboard in RDP session to match UK Macbook keyboard
POSH1Liner – Remove all Resource Groups and contents
Ever had a need to clean up and remove a bunch of resource groups and all the resources they contain? – often a problem after a period of frequent, err experimenting/failing.
CAUTION – use at your own risk, this could easily wipe out all your resources – even the stuff you want
1st – check you’re targeting the correct subscription – use
Set-AzContext -SubscriptionId <YOUR_SUBS_ID>Then – MAKE SURE You have the correct -Name pattern. If you omit the -Name parameter you’ll delete EVERYTHING in the target subscription (although it will prompt for a yes/no on each one to be safe (you can add the -Force parameter to not do this if you’re feeling brave)
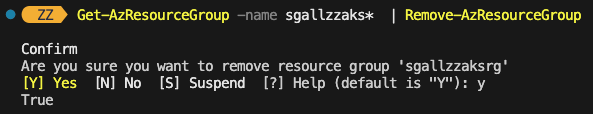
In this example all my RGs start with myResources (myResources1, myResources2 etc.) and we use a wildcard ‘*’ to do this pattern matching.
Get-AzResourceGroup -name myResources* | Remove-AzResourceGroup
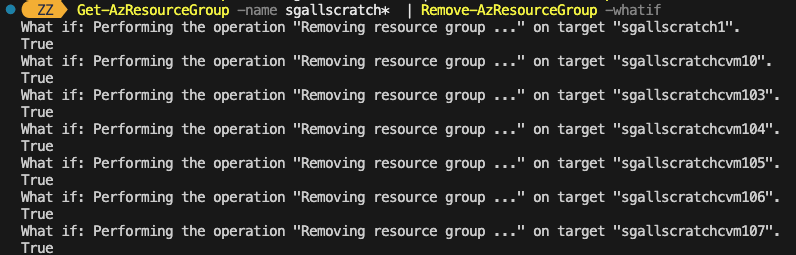
If you want to do a dry run to be absolutely sure which resource groups it will delete you can also add the -WhatIf parameter to the Remove-AzResourceGroup command
Convert Azure Key Vault from Standard to Premium
Had to do this earlier, I’d accidentally created a standard AKV instance and I wanted to make it premium to benefit from hardware backed key storage (required for a project I’m building), the az cli command to do this is as follows:
az keyvault update –set properties.sku.name=premium –name “YourAKVName” –resource-group “YourResourceGroup”
Use gping to graph HTTP response times
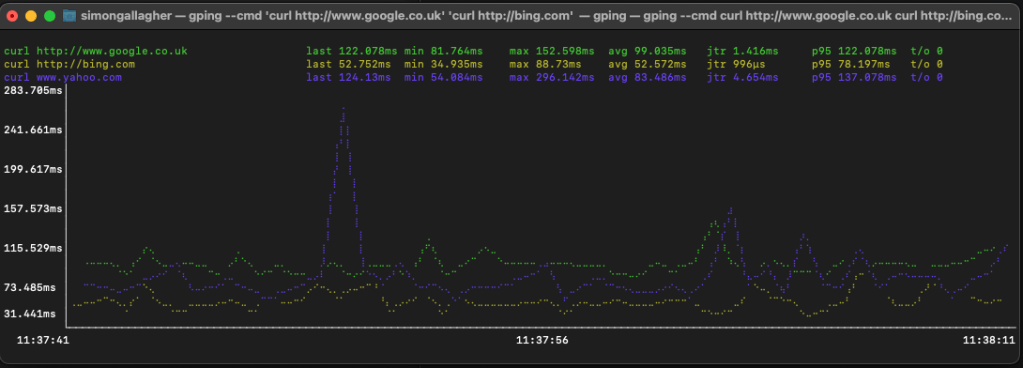
This is quite neat trick, as part of my standard home office setup I have a window on one of my screens showing a realtime gping to an Internet DNS server and my router, this allows me to quickly see if I have a burst of Internet latency, or maybe a home LAN/router problem – this is really useful when presenting something in Teams or similar as you can see real-time where you may have a problem without having to fire up a terminal and go fishing.
I discovered today that you can also use gping to graph the response time of a command, for example the docs give the example of gping –cmd ‘ls’ ‘ls /’ to show the differences between those two commands.

You can use this method to extend your simple real-time monitor beyond just ICMP (ping) by calling the command line http tool curl. this is possible because curl exits when it returns the HTTP payload from the server you point it at.
For example, using this command
gping --cmd 'curl http://www.google.co.uk' 'curl http://bing.com' 'curl www.yahoo.com' ..you can monitor response times from 3 popular Internet search engines from your PC. (yes, there are global load balancers and other infrastructure which can [re-]route the traffic transparently to you) but it’s a very simple and useful measure of your end-user experience of latency from where you are on the Internet to places you use.
Make Excel show phone numbers correctly
Should you have a requirement to export logs from say a Teams phone system to Excel for some analysis you’ll see that by default it interprets the ‘+’ International dialling symbol and turns the number into a scientific one – which isn’t very handy.
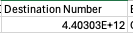
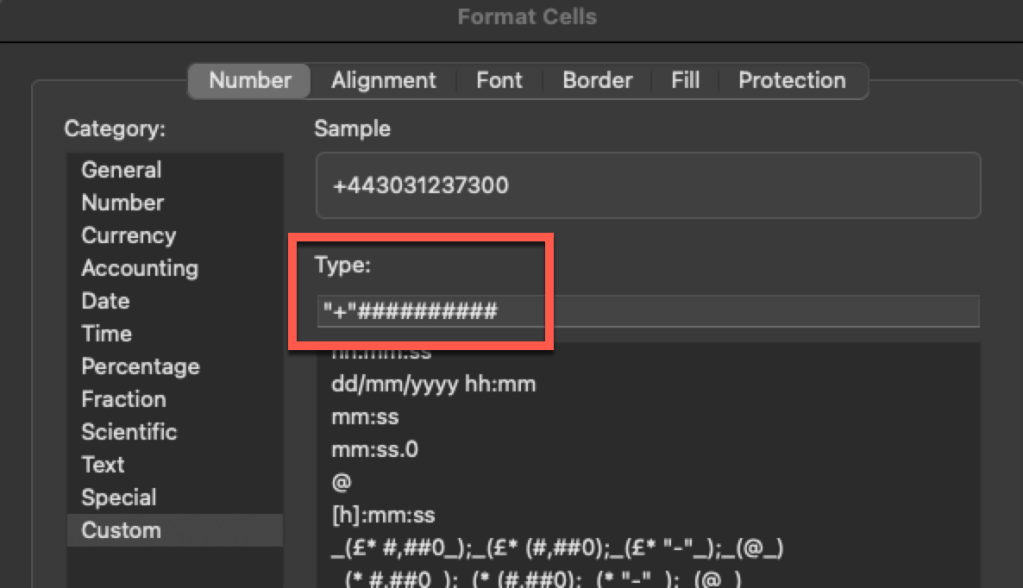
At least on my Mac none of the ‘canned’ formats Excel offers seem to be able to decode the numbers (Not checked in Windows Excel recently), to work around this I set the format to ‘custom’ with the following value to make it show correctly.
"+"##########
This results in

…Which, is the number for Buckingham Palace should you have any business with the king 🙂
Paste multi-line shell commands via SSH session
On occasion I have a bunch of commands to run inside a Linux VM over an SSH session from my Mac terminal (Zsh)
It’s tricky to get a variety of commands to reliably execute sequentially – some seem to trip over each other depending on how they handle i/o and this is a problem if you have something that is dependent on the previous command being completed.
Yes, I could copy the script to the server, chmod and run as a .sh bash script, use a proper CD toolchain etc. but I’m lazy and used to doing it this way from my Cisco days plus it also avoids leaving debug scripts on servers you’re working with 🙂
I’m sure there is a better way to do this, but I find this works really well.
SSH to your chosen Linux server
When you’re ready to go type an open brace “(”
Paste your command in
then close the brace “)”
and hit Enter.. and off you go all commands are executed sequentially and one by one.
Why has my Amazon Alexa device stopped announcing when people press my Ring doorbell?
If you have a Ring doorbell and have it ‘paired’ with Alexa so that when someone presses the doorbell it announces ‘there is someone at the front door” (or whatever) and it has stopped doing-so it may be that someone* has set your Echo device to ‘do not disturb’.
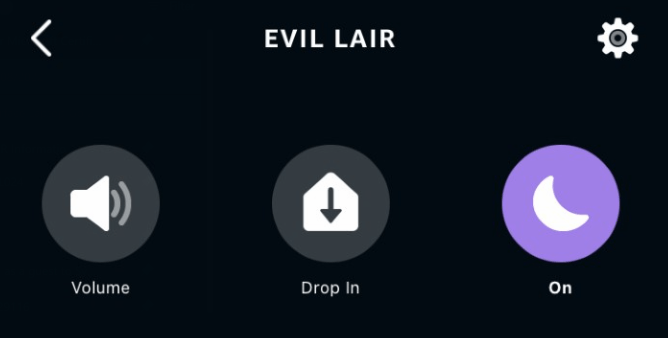
In the Alexa app you can change it by tapping the moon icon to turn it off

*in my case I did it to stop kids using ‘drop-in’ to the Echo device that runs music in my office to demand snacks or complain about the WiFi, but then forgot about it.
List all Azure Regions from CLI
Useful command, parked here for next time I forget how
az account list-locations --output table
Also possible to output as JSON etc, by adjusting the --output parameter